If you were directed to this website by a support ticket please send us an email at support+cac@truststack.us so we can assist in enabling CAC Authentication for our customers.
Before we start
Note: “CAC Authentication” is known as “Client Certificate Authentication”, "Mutual TLS Authentication" or "mTLS" outside of the DoD.
This is almost always a network issue, and this issue will happen for each network independently of any other network that is used. If you fix it on one network that will not fix it on another network.
On-site using a hardwired connection is a separate network from VPN.
If your VPN lets you choose separate servers, each one is a separate network.
If CAC Authentication is fixed for an on-site network and users on-site can now use CAC Authentication, this has no impact on a VPN, they will still have issues connecting.
If CAC Authentication is fixed for “VPN Server West” and users on “VPN Server West” can now use CAC Authentication it will have no impact on “VPN Server East”.
Where the problem happens with CAC Authentication
There are 3 primary causes for CAC Authentication to fail:
- Web Content Filtering / Break and Inspect
- Misconfigured Proxy
- Anti-Virus Software
Web Content Filtering / Break and Inspect
Web Content Filtering is when DISA (or another entity) inserts itself between a network and an external server.
It does this by breaking the encryption that TLS/SSL starts so that it can be inspected (hence the name "Break and Inspect") and then re-encrypts it when connecting to the external server. When the encryption is broken all information about CAC Authentication is lost.
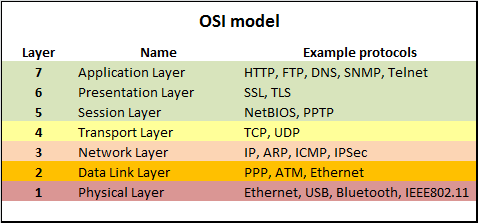
In terms of the OSI Model, this modifies layer 6, as stated above CAC Authentication needs layer 6 to be unmodified.
Misconfigured Proxy
Many times a proxy is used to facilitate security compliance and reduce bandwidth.
The DoD primarily uses Menlo's cloud proxy you can read about it here https://www.menlosecurity.com/press-releases/disa-awards-by-light-team-198-9m-cloud-based-internet-isolation-production-ota/.
The problem happens because many proxies by default will stand in between the browser and the external server and it only provides a proxy for the http protocol. This is a problem as we need the TLS protocol to be proxied. The above process for CAC Authentication gets reduced to this:
- The user navigates to a website that accepts CAC Authentication, through the proxy
- The website requests the browser to provide a certificate.
- The proxy ignores the request for the certificate
- The website then sends the webpage to the browser, through the proxy
In terms of the OSI Model, this only proxies layer 7, as stated above CAC Authentication needs to communicate on layer 6.
With any proxy there is a rule list that determines how the proxy works with each website, usually this is controlled network-wide. For DoD networks individual military bases usually do not have control over this (for example the 26 NOS (Network Operation Squadron) controls the lists for USAF/USSF bases).
Anti-Virus Software
Some consumer Anti-Virus software will act as one or both of the above. No DoD networks use this type of anti-virus software.
If you are on a personal machine on your home or another public network try disabling your anti-virus and attempting to authenticate.